If you wish to contribute or participate in the discussions about articles you are invited to contact the Editor
Galileo Open Service Navigation Message Authentication
| GALILEO | |
|---|---|
| Title | Galileo Open Service Navigation Message Authentication |
| Edited by | GMV |
| Level | Basic |
| Year of Publication | 2021 |
Galileo OS-NMA (Open Service – Navigation Message Authentication) represents an GNSS Authentication and encryption mechanism that allows a GNSS receiver to verify the authenticity of the GNSS information and of the entity transmitting it, to ensure that it comes from a trusted source. Authentication is an intrinsic GNSS capability remaining internal to the GNSS receiver, without any new interfaces to the avionics.
Galileo OS-NMA will be a free-of-charge service which will become available in the near-term evolutions of the Galileo Full Operational capability (FOC), potentially for 2022-2023.
Introduction to Galileo OS-NMA feature
Galileo OS-NMA feature consists of digitally signing the Open Service Navigation message in the E1 band, making use of forty reserved bits (“Reserved 1”) in the Galileo E1B data message (I/NAV) and the Timed Efficient Stream Loss-Tolerant Authentication (TESTA) protocol[1], thus keeping the rest of the navigation message unencrypted[2] . The use of these reserved bits allows backwards compatibility with older versions of the navigation message ICD.
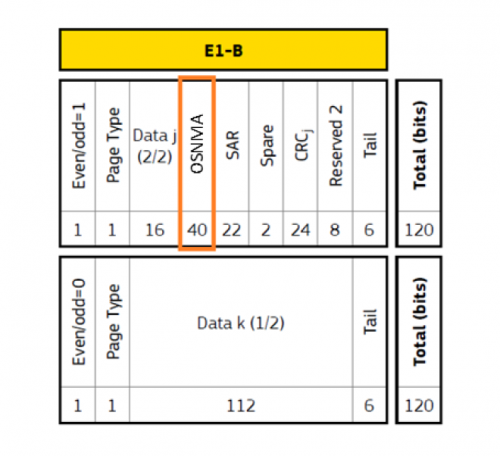
The OSNMA field is composed of two parts:
- The HKROOT section (first 8 bits) includes the global headers and the Digital Signature Message (DSM.
- The MACK section (next 32 bits) contain the MACs and associated keys, delivered later.
TESTA protocol
Galileo OS-NMA authentication capability is based on the use of TESTA protocol. One of the greatest advantages of this protocol is that it requires low bandwidth to transmit the authentication information, together with a tolerance to data loss in case a message is lost.
The main idea of TESLA protocol is that the key used in the authentication process belongs to a chain generated using a one-way function F, also called hash function. The chain starts with a secret seed key; and each element of the chain can be constructed by hashing the previous element. This one-way function cannot be used to predict keys. This implies that the receiver must possess some information (the root key) certified as correct independently from the information sent through the Signal in Space.
The TESLA used for Galileo OS-NMA has been optimized to use a single key for all the satellites, so users will be able to receive the key by any satellite in view. This opens the door to authenticate non-Galileo GNSS satellites.
Authentication based on Galileo OS-NMA
The way in which authentication based on Galileo OS-NMA works can be summarized as follows:
- The receiver demodulates the navigation data and a Message Authentication Code (MAC) that authenticates the plaintext navigation message.
- The key required to authenticate the MAC is broadcast by the system with some delay.
- The receiver demodulates the key.
- The receiver authenticates the key with a previous key from the chain that is considered authentic or from the root key. As explained before, this key is part of a pre-generated one-way chain whose root is public, and which is transmitted in reverse order with respect to its generation
- The receiver re-generates the MAC key with the data, which should match the previously received MAC.
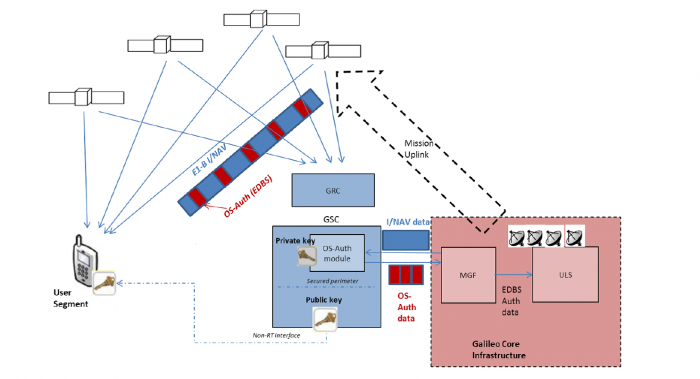
A summary of the proposed Galileo OS-NMA architecture is shown below.
Credits
This article has been created based on Galileo Navigation Message Authentication Specification document[2] and other information as indicated through references.
References
- ^ I. Fernández-Hernández, V. Rijmen, G. Seco-Granados, J. Simon, I. Rodríguez, and J. David Calle, “A Navi-gation Message Authentication Proposal for the Galileo Open Service,” Navigation, Journal of The Institute of Navigation, vol. 63, no. 1, pp. 85-102
- ^ a b c Galileo Navigation Message Authentication Specification for Signal-In-Space Testing v1.0
- ^ Guidelines OS-NMA implementation in smartphones, Moises Navarro Gallardo, Airbus
